CrowdStrike Falcon® Cloud Security now delivers real-time detections for AWS IAM Identity Center, helping organizations detect and respond to identity-driven cloud threats before they escalate.
A few months ago, we released CrowdStrike Falcon® Identity Protection support for AWS IAM Identity Center to help organizations detect and stop identity-based attacks before they could reach the cloud control plane. Now, we’re expanding that protection by bringing select identity threat detections directly into Falcon Cloud Security. This gives customers the ability to stop cross-domain attacks earlier — without requiring an additional investment.
Adversaries no longer operate in silos, and neither should defenders. Modern cross-domain attacks may start with stolen identities and end with full cloud control plane compromise. Threat actors like SCATTERED SPIDER use valid credentials to bypass traditional defenses, escalate privileges, and seize control of critical cloud resources. The evidence is in our data: The CrowdStrike 2025 Global Threat Report found 35% of cloud incidents in the first half of 2024 stemmed from valid account abuse. Meanwhile, the market for stolen access is thriving, as evidenced by a 50% year-over-year increase in access broker advertisements.
To stay ahead, organizations need a unified security approach across identity, endpoints, and cloud workloads. Read on to learn how we’re helping them break down silos with the CrowdStrike Falcon® cybersecurity platform.
Bringing Identity Threat Detection to Falcon Cloud Security
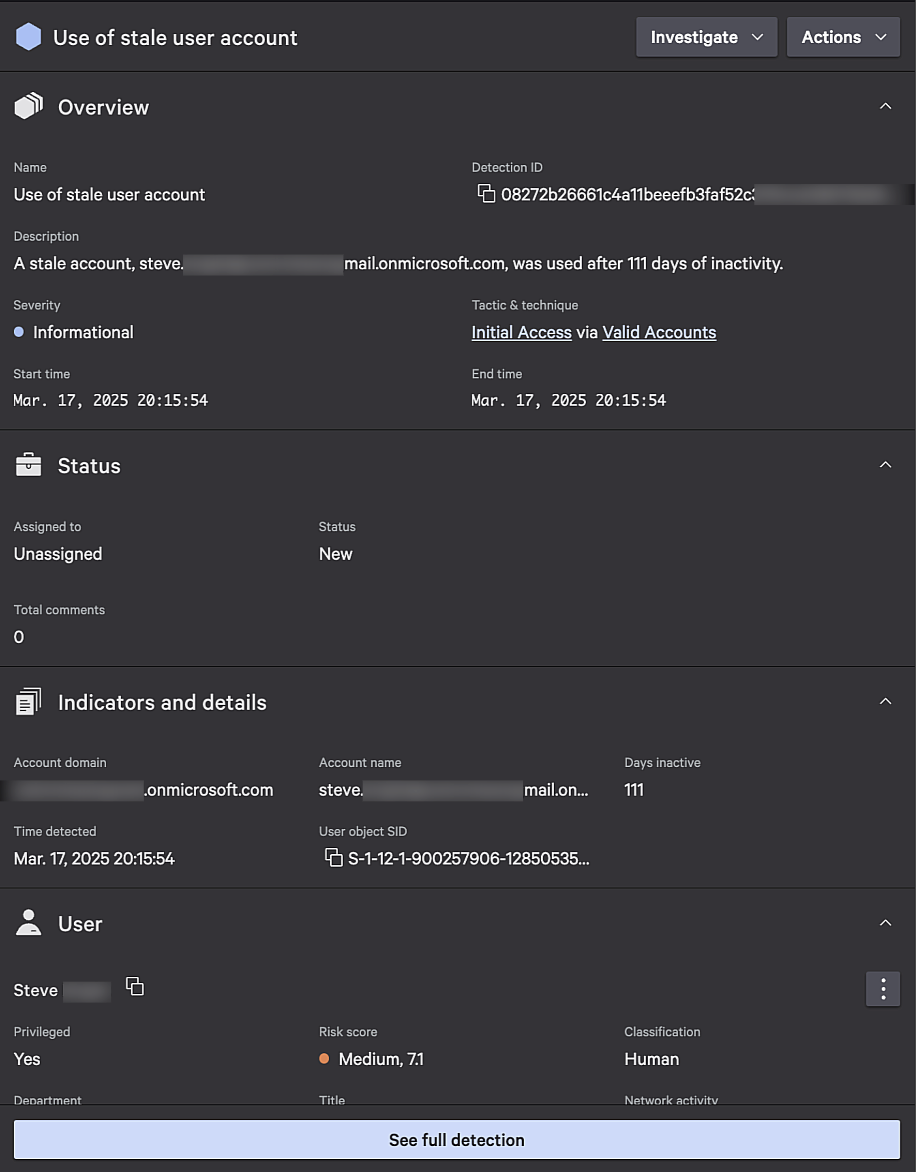
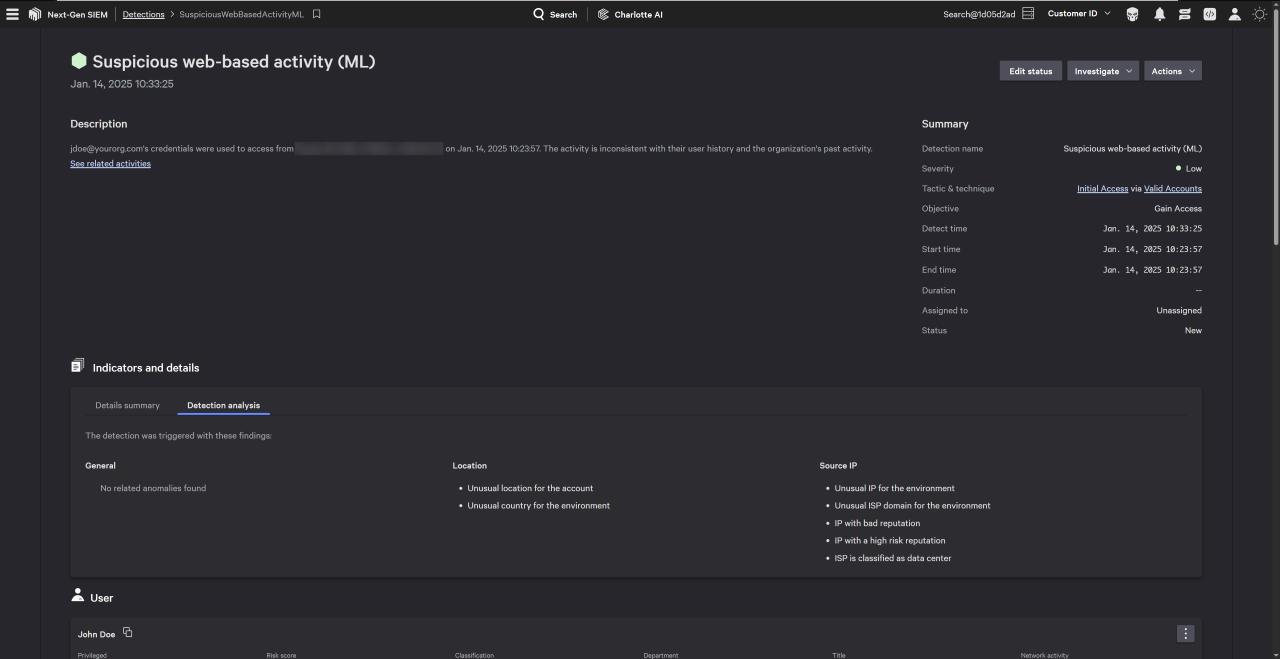
With this release, Falcon Cloud Security customers gain built-in detection capabilities for AWS IAM Identity Center, allowing them to spot and respond to suspicious authentication activity in real time. These detections help identify key identity-based threats, including:
- Access from unusual location: Detects logins from unexpected locations, a common indicator of compromised credentials
- Access from multiple locations concurrently: Flags attempts to use the same account from different regions simultaneously
- Access from an IP with a bad reputation: Identifies logins originating from known malicious or high-risk IPs
- Suspicious web-based activity: Highlights unusual authentication behaviors that may indicate an account takeover or an adversary-in-the-middle attack
- Use of a stale user account: Alerts to access attempts from inactive or previously unused accounts, which adversaries often exploit





![Helping Non-Security Stakeholders Understand ATT&CK in 10 Minutes or Less [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/video-ATTCK2-1)
![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/Edward-Gonam-Qatar-Blog2-1)